- Back to Home »
- Cracked , hacking , Tutorials »
- Keylogging-complete guide
Posted by : Unknown
Saturday, 27 October 2012
NOTE: This is only for educational purposes,I'm not responsible for any of the damage caused.
KeyLogging:
It is a method of tracking the keys struck (typed) by the user on the keyboard and saving them as logs for viewing them later.
Keyloggers:
These are used to achieve key logging.they basically interpret the inputs sent through keyboard.though the previous definition of keylogging does no0t apply to modern keyloggers because,they are able to do a lot more than just recording key strokes.they can take snapshots,record app data,and some advanced keyloggers are also capable of recording the entire screen.There are two types of keyloggers:
- Hardware key loggers
- Software key loggers
- Hardware key loggers:
The above shown is a typical key logger.As you can see it is bridged between the keyboard and the cpu jacks.it reads the Electrical signals it receives from the keyboard,keeps a copy in it,and sends a copy to the cpu .those logs can be later retrieved by reversing the connection sockets physically.some advanced Hardware keyloggers are able to connect to a near by hotspot and send the logs to your email.And as you may expect,one need to buy them and they can also cost a buck more if you want a fully functional one. And they also come in various shapes and sizes,even some come in a USB flavour,i.e,all you need to do is,plug it in the usb port and they start recording the keys.
Prevention:
- Check out for any suspicious hardware attachments especially when using computers in cybercafes,or any other public places.
- Use virtual Keyboard.To access Virtual Keyboard in windows, press win+u,then select On-Screen Keyboard.
Software KeyLoggers:
They are widely used keyloggers,because of their ease of access and even they have many more advantages over Hardware Keyloggers. They are installed on the system which we want to track with an ease.Let us consider an example.below,i'm using " Blazing Tools Perfect Key logger".There are two ways of using it:
- Direct installation
- Remote installation
- Direct Installation:
- This method is to be followed when you have Physical access to the system you want to monitor.
- First of all,you have to Download and install it.Download it from here (or you can get our new version of Actual spy keylogger )
- Then open the installation folder of Perfect keylogger,it would be something like, "C:\Program Files \BPK " then Replace the patched exe with the original one in the installation folder.
- Run the key logger and register with the following details:
Name: mrsmartypants
Registration code: 007A-DF26-GV05-FHI0
- Right click on it from toolbar
- Click on options,Now make the following changes
- If you can understand what we are trying to do,we are just trying to make it undetectable.And remember the key combination used to show/hide the programe icon so that you can access it later.
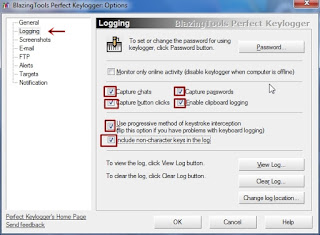
- Now navigate to Logging section and make the following changes
- You can set a password if you want to prevent others from accessing it,by clicking on the password button and setting a password.
- Here,we are saying what data is to be recorded
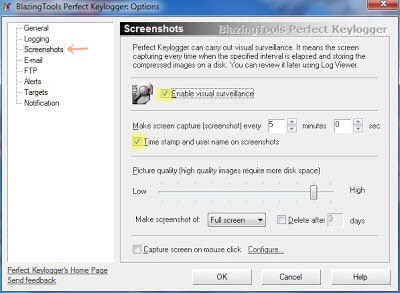
- Now Navigate to Screenshots(only if you want to have screenshots)
- Here you can set the time interval between screen shots,quality etc.
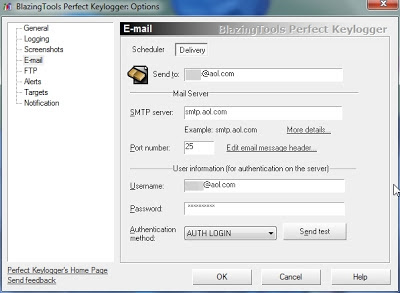
- Now navigate to E-mail and make the following changes.
- You can set the time interval after which logs should be sent to you,and include the data which you want,and make the log file format to HTML.And we are using clear log after successful sending option because we don't want the data to be accumulated and raise a suspicion.But the disadvantage is,after every 30 min,the logs are destroyed,so if the computer is not connected to internet,at that time,you'll not receive any logs pertaining to that time slot.
- Now navigate to Delivery tab and ,make the following changes
- You need to have an aol account to receive remote logs.and in the user information coloumn,you need to enter your original aol usename and password.Then you can send a tst mail to check wether it works or not.
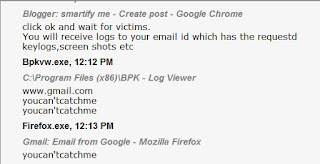
- And then,you are done.now click ok and wait for victims.
- You will receive logs to your email id which has the requestd keylogs,screen shots etc
- The log files will look similar to the above shown pic.you need to do a little bit of guessing work to differentiate between usernames and passwords and to completely understand the logs.
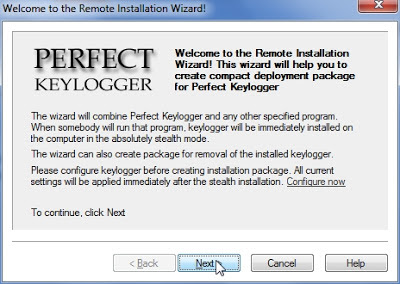
Remote Installation:
- It can be used when you don't have physical access to the victim's pc.
- First you need to install the keylogger on your system(i suggest you disable anti virus for its smooth running) and configure it with the above mentioned settings.
- Then again right click on the perfect keylogger icon from the tool bar and select Remote installation
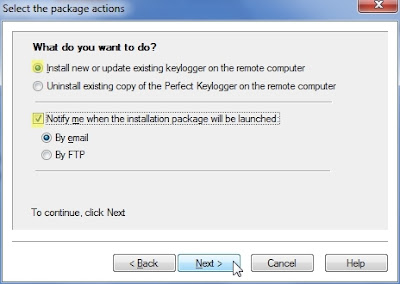
- You need to select an application with which you want the keylogger to be binded with
- This is completely optional.you can skip it
- After the package is created,you can find it in the same folder as the application you've selected,but with a small change in its name.alol you have to do is send that package to victim and wait for him to install it,then you will start receiving logs from his system.
Prevention:
- Use on screen keyboard
- Run an updated Anti virus software
- Do not accept any software from unknown sources
- Scan software with an antivirus before installing it.
Just imagine what you can do with keyloggers in this world which runs by passwords,you can compromise many social networking accounts,mail accounts,or even Bank Accounts.So,be smart,save yourself from the world.
Download Perfect keylogger full version
Other Good Keyloggers:
Key loggers part2
.jpg)







BPK+-+Log+Viewer_2012-10-27_12-14-03.jpg)